

Since September 15, 2003:
Are you receiving e-mails like this one? They are dangerous counterfeits.
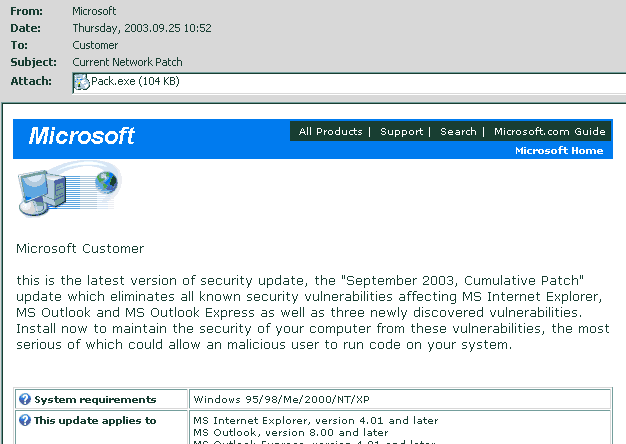
Many who weren't fooled before were fooled by this one.
Microsoft will never e-mail a patch to you unsolicited. If you want to install a patch, you have to download it from Microsoft.
On that basis alone, you know that this message cannot be for real. It look very official and authentic, but it is counterfeit and it does bad things to your computer, invading your privacy etc. Once infected it shows bogus error messages in order to scam more information from you.
Don't be gullible, and don't trust messages like this one. If you execute a patch or program sent to you by a stranger, you can be giving them control over your computer. With information from your computer they can damage you in the real world. E-mail generally cannot be authenticated. This fake message is not from Microsoft or anyone trying to help you.
The counterfeit is message sent to you by an infected computer in an effort to spread the virus.
The "patch" in this case is really a virus known as "W32.Swen.A@mm".
For more information, see these links: Tech info on Symantec News info on Google
If you launched the attachment and it ran, you have a serious problem. [If Anti-virus blocked it, you are okay.]
Note, the attachment also attempts to execute itself even if you only view it or "preview" it, thanks to an old vulnerability in some e-mail programs. Unless you are protected in some way, you could be in trouble even if you only previewed the message. [If you have applied Windows Update ( http://windowsupdate.microsoft.com ) after a certain date (at last a year ago, then the attachment can't launch by itself and you are okay.] [If Anti-virus blocked the program from running, you are okay.]
For best security, you need to keep up-to-date with Windows Update (plus use careful practices), or keep up-to-date virus protection, or better yet, both.
[[If you receive any e-mails with .exe attachments, it is the fault of your ISP or administrator. Up-to-date e-mail security requires that incoming mailservers take specific action on all e-mails with .exe attachments. There are basically two good options. The best choice can vary according to circumstances. (1) The mailserver can strip out the attachment and add a suitable warning that the message was Probably counterfeit and Probably a virus. (2) The mailserver can Refuse the message (Refuse with an explanation about the attachment, in case the sender was legitimate.) (Note: Refuse, NOT 'bounce'.) For a mailserver to let in e-mails with .exe attachments is reckless irresponsibility on the part of whoever administers or neglects those mailservers. No one has any reason to send you an .exe file attachment. Anyone needing to send an .exe file will know how to zip the .exe file, and anyone needing such a file will know how to unzip the file.
Many other attachment file types are able to cause problems and usually only sent by viruses or attackers. They include but are not limited to .exe .com .bat .pif .scr
Outbound mailservers should also refuse messages with the dangerous attachment file types, for the same reason.]]
2005.04.22
A new computer virus is going around.
It has been active since April 2002, and it is not decreasing in incidence as has happened with previous viruses.
It is spreading because it has made some virus advise obsolete. "Not opening attachments" is no longer enough, because this new one uses a trick to make attachments self-opening.
It is said to have infected 7% of all computers and is generating possibly 5% of all e-mail traffic.
It is more than a nuisance.
It sends out copies at random of files or webpages you are viewing or editing.
It stops some software from running, and can stop the computer from working completely.
On some days of the year it might delete files on every drive it can access.
It can infect most versions of Microsoft Windows, unless they have been updated or protected.
If we have e-mailed you this message, your computer might already be infected, or your computer could get infected tomorrow. Infected computers constantly send e-mail that tries to infect other computers.
The name of the virus is "W32.Klez.H@mm". You can look it up on any search engine. Several credible sources have issued reports on it.
Protections are not being placed in the Internet where they need to be. However, each individual can do a lot to protect their own computer. If we can protect our computers, we will be the people with the solution, and stop being part of the problem.
It is free and fairly simple to find out whether your computer is infected with this virus.
(It is free and a little less simple to cure your computer if it is infected.)
It is free and fairly simple to prevent future infection of your computer by this and more dangerous viruses.
Here is how.
Is My Computer Infected?
If your computer was protected, there is a good chance your computer is not infected by W32.Klez.H@mm . There are several kinds of protection; any one protection is enough. If your computer always ran working, up-to-date anti-virus software, you were protected. If you kept your computer updated with Windows Update AND you did not open attachments, you were protected. If your incoming e-mail has always come through a mailserver that has been protected by an up-to-date e-mail anti-virus software, you were protected.
If you had no protection and you received even one e-mail infected with W32.Klez.H@mm, AND you opened or pre-viewed the message, your computer probably is infected.
One simple test is, look for a specific file in a specific folder. The catch is, the folder name varies and the file name also varies. You have to look in the "system" folder. In Windows 95 Windows 98 and Windows ME, this folder is usually C:\WINDOWS\SYSTEM . In Windows NT, Windows 2000 and Windows XP, the folder is usually C:\WINNT\SYSTEM32 . The file name starts with WINK and ends with .EXE ; in-between are two to four randomly chosen letters. For example, WINKAB.EXE . You can do this search from the Windows file-search by browsing to the right folder and searching for wink*.exe . You could also search from the command prompt.
Other signs of infection: (These are less certain, as they could have other explanations.) Your computer is a little sluggish or crashes more often. Frequent activity on the modem or cable modem when you are not doing anything on the computer. You get lots of bounced e-mail or people whom you write to get lets of junk e-mail.
Note, just because you get e-bounced mail does not mean you are infected. The virus uses random addresses from someone else's address book for both the "To" address and the "From" address.
Removing The Virus.
More than one major anti-virus software vendor has chosen to give away a remover for W32.Klez.H@mm and other related viruses.
I used the one from Symantec, successfully, on a computer running Windows 98. It is available here:
http://securityresponse.symantec.com/avcenter/venc/data/w32.klez.removal.tool.html
Notes: Pay attention to the instructions. The Safe Mode reboot is important, or else the removal will need to be done a second time. Launch by double-clicking, as they recommend. Running the remover from a command prompt might go wrong. Also, review the list of "repaired" files. Most of the "repaired" files were actually ruined. Some applications may need to be re-installed.
Download the remover only from the website. E-mails that claim to be fixes are actually infected messages.
Resisting This and Other Viruses:
There are 4 methods of resisting viruses. No one of them is 100% effective. Each method covers a separate aspect of protection.
1) Safe Practices
The message is always, do not open attachments. If necessary, with knowledge and care.
Whatever the attachment seems to offer, from someone you don't know, how could it be anything you want or need? More likely it is a dangerous file that will attack your computer in some way, IF you open it. It is not worth the risk.
If the attachment seems to be from someone you know, there is still a chance it is NOT REALLY from anyone you know, but was sent by a computer virus as an attack on your computer. For the most part, not opening the virus means you cannot be infected by the virus.
If the attachment IS from someone you know, you still need to be cautious. They could accidentally send you an infected file.
If the attachment claims to be from Microsoft, it is not. Microsoft would not e-mail patches unsolicited. That is one ploy of the virus.
Files that are especially dangerous end in .bat .com .exe .pif .scr . Files that are generally not dangerous end in .txt .jpg .bmp . (Possible risk are .doc and .xls because of the "macro viruses", which I won't go into here.)
Some files try to hide their type by using a double extension. For example, message.txt.exe or empty.doc.pif . These two files would be dangerous attachments. The LAST extension is the one that counts, so both are dangerous.
If the computer is shared, everyone who uses it must follow the same rules. Even once opening the wrong attachment ruins the computer's security, for everyone.
Many people follow the safe practice of not opening e-mails, but it suddenly it is not enough. The breakthrough discovery that made W32.Klez.H@mm so prolific is, it fools the computer into executing the attachments. The Windows software contained a loophole or vulnerablilty that allows this. There is a patch that can fix this vulnerability, but after the patch is in place, the same rules must be followed, do not open attachments. That these vulnerabilities keep showing up is certainly tragic and even suspicious, but that is another topic.
Even with all of the other protections in place, not opening attachments is still a good idea. Not opening attachments can protect from new vulnerabilities that Windows Update has not closed. Not opening attachments can protect from new viruses that the virus scanning software might not recognize.
2) Windows Update
Visiting the Windows Update website is a great idea. It is free. It is important. Whenever a new virus is discovered, a new vulnerability is usually discovered along with it. After a patch is released to fix the new vulnerability, generally the whole thing is disclosed in detail. Often, this information is used by other malicious people to devise new viruses, especially if it they see that people are not hurrying to apply the fixes as soon as they are made available.
The updates can take some time to download; that is the only real drawback. Your computer gets updated to close the known vulnerabilities. This can protect from any number of infections that could potentially slip past virus scanning software or safe practices.
Additionally, Windows Update closes up other kinds of vulnerabilities -- those that could allow your computer to be attacked by "malicious web-sites" and more.
You can visit Windows Update from Internet Explorer -- you can click on Tools:Windows Update, or you can jump to this web address:
http://windowsupdate.microsoft.com
3) Anti-virus software
The good ones cost money. (If some are free that are any good, I cannot say.) Some people will go for it, some will not. The good news is, you still can be reasonably safe if you use some of the other safeguards.
For the virus software to be effective, you have to UPDATE the virus definitions. Generally the virus software can only protect against viruses that it knows about.
Some software might includes a generic protection against e-mail attachments, removing or re-naming attachments that are dangerous because of the filetype. This aspect of the software does not need constant updating.
Anti-virus software can make a nearly complete protection of a computer even if it has not had Windows Update applied, and if safe practices are not followed at all.
4) Firewall software and/or hardware
There is a very good firewall software called "ZoneAlarm". It is FREE. It is available at http://www.zonelabs.com .
Just follow the links for "Free ZoneAlarm".
This software, if used correctly and watchfully, detects the KLEZ infection. With no other protection, after infection occurs, it will pop up a messge asking "Do you want to allow WINKAB.EXE to access the Internet?". This is not a very specific warning, but to a watchful user it is a clear indication something has happened. If you did not install new software and a pop-up comes up for new software, then a new infection is a possible cause. A little research shows that the file was put there by the KLEZ infection. Going back to the question from Zone Alarm, if I answer yes, then the KLEZ infection will start mass e-mailing everyone in my Windows address book. If I answer no, then it cannot. Still, I will have to take action about the infection.
Zone Alarm helps in another way. The KLEZ infection actually tries to shut down some parts of ZoneAlarm. When ZoneAlarm closed its screen icon, this was actually the first indicatiojn I had seen of something gone wrong. The second indication was that someone had authorized the WINKAB.EXE application to access the Internet. The final proof was, I checked mail in Outlook and received 400 bounce messages.
Internal firewall software also provides warning about attempted attacks or scans from other computers on the Internet (happens all the time). By blocking the incoming messages and by blocking internal software from listening for the messages, ZoneAlarm can close a whole class of vulnerabilities.
However, ZoneAlarm does protect against operating system vulnerabilities or infected attachments or users who open attachments.
It will take a lot before this new virus stops propagating. Unfortunately there is a dilution of responsibility. If every computer gets updated and stays updated, the virus will die out. If every outbound e-mail server refuses e-mail with certain attachment types, the virus will die out. If every inbound e-mail server refuses e-mail with certain attachment types, the virus will die out. Any one fix would solve the problem entirely. Unfortunately there will never be 100% coverage of any area. At best MOST individual computers will be updated, MOST outbound servers might be updated and MOST inbound servers might be updated, so there will always be a way for the problem to propagate. One solution might be, if there was a small number of master e-mail servers on the Internet, those servers could be kept up to date. But centralization is not what the Internet was ever about.
The best I can advise is, update and maintain what you have control over. And press others to update what they have control over.
sites that include removers:
http://securityresponse.symantec.com/avcenter/venc/data/w32.klez.h@mm.html
http://www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=WORM_KLEZ.H
reports or warnings:
http://vil.mcafee.com/dispVirus.asp?virus_k=99455
http://www.nipc.gov/warnings/alerts/2002/02-002.htm
http://toronto.virusbtn.com/magazine/archives/200207/klez.xml
You can research it yourself -- www.google.com
page added 2002.07.31
last edited 2005.04.22